CYBERSECURITY SUPPLY CHAIN RISK MANAGEMENT
We provide a wide range of services
Apart from providing security services, the next best thing we offer is our consulting service for cybersecurity supply chain risk management.
CYBERSECURITY SUPPLY CHAIN RISK MANAGEMENT and you?
Wyvern Security specializes in Cybersecurity Supply Chain Risk Management (C-SCRM), a critical process that safeguards organizations from cybersecurity threats within their supply chains. They offer comprehensive services, including risk assessment, vendor due diligence, incident response planning, and compliance verification. Wyvern Security ensures that your supply chain remains secure, resilient, and aligned with industry standards, protecting the integrity of your products and services as they traverse the complex supply chain landscape. Their expertise lies in continuous monitoring, collaboration, and adaptability, enabling them to address emerging cyber threats and changes in your supply chain effectively. Partner with Wyvern Security for unwavering cybersecurity in your supply chain.

Why Cybersecurity Supply Chain Risk Management?
Cybersecurity Supply Chain Risk Management (C-SCRM) is a pivotal and proactive process, expertly navigated by Wyvern Security, crucial for safeguarding organizations against the evolving landscape of cyber threats within their intricate supply chains. It ensures data protection, business continuity, and regulatory compliance, while also mitigating financial and reputational risks. In today's interconnected world, where supply chains are complex and digital, C-SCRM serves as an essential defense against potential cyberattacks and vulnerabilities that could disrupt operations and compromise sensitive information. Wyvern Security excels in this domain, ensuring the security and integrity of products and services throughout the supply chain journey
Wyvern Security’s Expertise in Cybersecurity Supply Chain Risk Management (C-SCRM)
C-SCRM stands as a pivotal process within an organization, vital for identifying, evaluating, and mitigating cybersecurity risks embedded within the intricate web of its supply chain. Wyvern Security excels in this domain, safeguarding the security and integrity of products and services as they traverse the supply chain landscape. Below are key facets of C-SCRM, expertly navigated by Wyvern Security:
Supply Chain Mapping
Wyvern Security takes a meticulous approach when illuminating the foundation of your supply chain. This critical step involves creating a visual map that unveils the intricate network of suppliers, providing clarity on the extensive array of products and services they contribute to your organization's operations. This map is not merely a static representation; it's a dynamic tool that continuously evolves as your supply chain expands and adapts.
Through this visual map, Wyvern Security brings to light the complex interdependencies and relationships within your supply chain ecosystem. It showcases the crucial connections between various suppliers and their contributions to your overall product or service delivery. Moreover, it reveals potential cybersecurity vulnerabilities that might lurk within this web of interactions.
By creating this comprehensive picture, Wyvern Security empowers organizations to make informed decisions about their supply chain cybersecurity. It enables proactive risk assessment and management by identifying potential weak points and areas that require reinforcement. This visual map serves as a valuable foundation for developing a robust Cybersecurity Supply Chain Risk Management (C-SCRM) strategy, helping you navigate the evolving landscape of cyber threats with confidence and precision.


Risk Assessment
At Wyvern Security, we recognize the unique cybersecurity risks associated with each supplier and vendor within your supply chain. Our rigorous risk assessments meticulously examine their security practices, historical performance, and the sensitivity of the data or services they handle. By scrutinizing their past incidents and vulnerabilities, we gain insights into their track record. We also evaluate their adherence to industry best practices, ensuring they meet the cybersecurity standards expected of your partners. This comprehensive approach empowers you with data-driven insights to make informed decisions, proactively manage vulnerabilities, and strengthen your C-SCRM strategy.
Vendor Selection and Due Diligence
At Wyvern Security, we recognize that onboarding new vendors or suppliers is a critical step in enhancing your supply chain's cybersecurity resilience. Our due diligence process serves as your protective shield, ensuring alignment with your cybersecurity standards. By scrutinizing potential vulnerabilities, assessing historical performance, and evaluating past incidents, we empower you to make informed vendor selections. This comprehensive approach fortifies your supply chain against threats, ensuring its continued security and resilience.


Security Standards and Contracts
In the realm of cybersecurity, clarity is paramount. Wyvern Security's approach involves embedding precise security standards within contracts to ensure unambiguous expectations. Our contracts go beyond legal documents; they become robust frameworks. This includes clear cybersecurity expectations, detailed incident response protocols, and defined repercussions for non-compliance. This proactive approach encourages all parties to prioritize cybersecurity and safeguards your supply chain effectively.
Third-Party Risk Assessment Tools
At Wyvern Security, we optimize our supplier cybersecurity assessments through the strategic deployment of third-party risk assessment tools and services. This approach broadens the scope of our evaluations, providing you with comprehensive insights into your suppliers' security landscapes. The rationale behind this choice is to ensure an objective and thorough examination of potential vulnerabilities while enhancing efficiency through expert-driven assessments. By harnessing these third-party resources, Wyvern Security delivers invaluable perspectives on your supply chain's cybersecurity. This empowers you to make informed decisions, implement necessary enhancements, and bolster your supply chain's overall resilience against cyber threats.

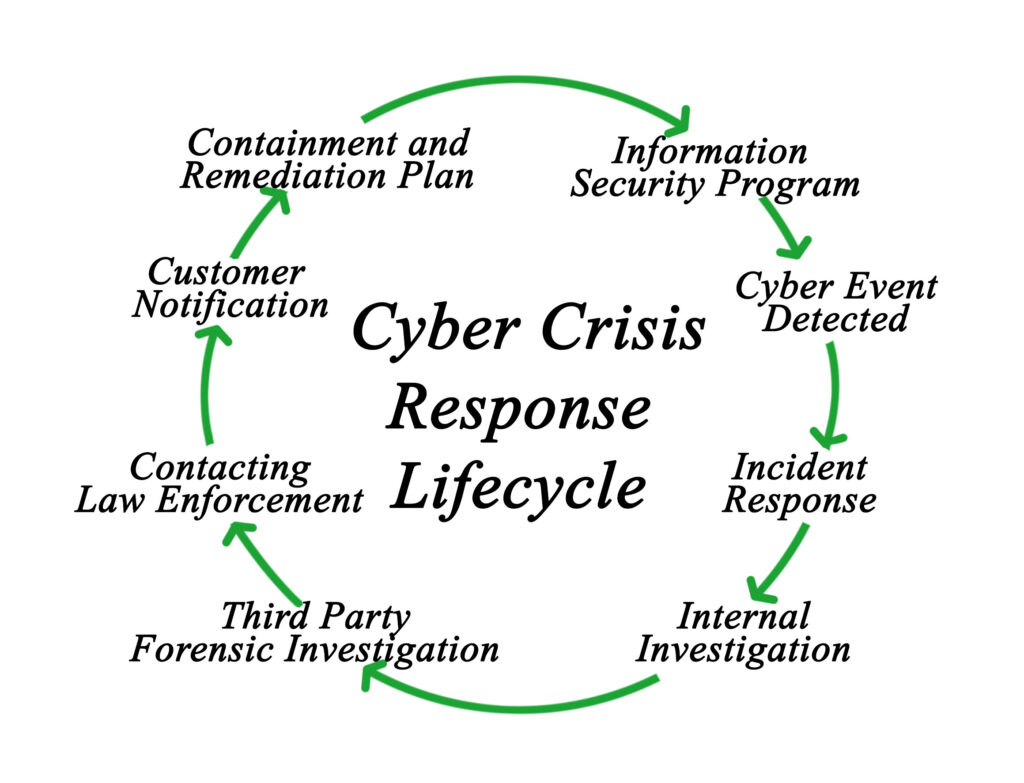
Incident Response Planning
Incident response planning is a core strength at Wyvern Security within our Cybersecurity Supply Chain Risk Management (C-SCRM) framework. We excel in crafting swift and effective response plans, ensuring seamless coordination with suppliers during breaches. Our expertise lies in developing efficient plans designed for unified action, reducing response times, and minimizing potential damages. With Wyvern Security's proactive approach and continuous refinement, you can confidently navigate the evolving cybersecurity landscape, safeguarding your supply chain's integrity.
Data Protection and Encryption
At Wyvern Security, we prioritize the meticulous safeguarding of digital assets. Our proficiency in Data Protection and Encryption, integral to our C-SCRM strategy, is underscored by our resolute commitment to bolster your organization against data breaches. Our approach hinges on the implementation of robust encryption techniques, which serve as a formidable bulwark against unauthorized access. Encryption transforms data into an unreadable format during transmission and storage, rendering it impervious to interception or compromise. We rigorously align our data protection measures with industry best practices and standards to ensure that your data security not only complies with but also surpasses the most stringent benchmarks. Going beyond encryption, we engineer comprehensive strategies that encompass access controls, multifaceted user authentication mechanisms, and secure data storage protocols, all tailored to your distinct requirements. With Wyvern Security's Data Protection and Encryption, your digital assets are not only fortified; they are fortified with the utmost technical precision, cementing the integrity of your supply chain at a granular level.


Supplier Training and Awareness
In the intricate realm of supply chain cybersecurity, knowledge and awareness are foundational. At Wyvern Security, we take a technical and strategic approach to Supplier Training and Awareness. Our belief is simple: informed suppliers are secure suppliers. We provide targeted training sessions tailored to your suppliers' specific needs, arming them with the technical skills and knowledge needed to safeguard their systems and data effectively. With access to a wealth of technical cybersecurity resources and our emphasis on fostering a collaborative security culture, we not only reduce risks but also elevate the collective resilience of your supply chain against the dynamic and sophisticated cyber threats of the digital age.
Continuous Monitoring
In the mathematical realm of cybersecurity, the principle of continuity defines our approach to Continuous Monitoring within our C-SCRM strategy. Just as continuous functions in mathematics have no breaks, our surveillance maintains an uninterrupted watch over your supply chain, 24/7. This mathematical rigor eliminates gaps and promptly identifies deviations from expected security baselines, enabling swift responses. Our approach also resembles derivatives in calculus, as we continuously scrutinize network traffic, system logs, and supplier compliance. This mathematical precision allows us to detect and assess changes in security threats, enabling proactive responses. Furthermore, our Continuous Monitoring accumulates data over time, similar to the integral concept in calculus. This forms the basis for proactive security measures, fostering a secure and cohesive supply chain ecosystem. With Wyvern Security's Continuous Monitoring, your supply chain operates with mathematical precision, safeguarding operations and fortifying resilience against cybersecurity challenges.


Incident Response Testing
Within cybersecurity, precision is paramount, and the concept of iteration forms the basis of our approach to Incident Response Testing within our C-SCRM strategy. Our dedication to this practice is rooted in a technical rationale: Our iterative approach ensures that incident response plans evolve progressively to become more effective and efficient over time, much like the refinement of algorithms. Through tabletop exercises and simulations, we validate the collaborative elements of the plan, harmonizing it with supplier participation. This anticipatory approach minimizes the potential impact of incidents and contributes to the overall resilience of your supply chain against cybersecurity challenges. With Wyvern Security's Incident Response Testing, your supply chain benefits from a technical and iterative approach that ensures your incident response plans are finely tuned, harmonized, and aligned with the dynamic cybersecurity landscape. This continuous improvement cycle helps minimize the impact of security incidents and reinforces the overall resilience of your supply chain from a technical perspective.
Regulatory Compliance
In the complex landscape of supply chain cybersecurity, Wyvern Security's commitment to Regulatory Compliance within our C-SCRM strategy is unwavering. We ensure that your supply chain cybersecurity practices align seamlessly with industry regulations and standards, acting as your shield against potential legal and financial repercussions. Beyond mere compliance, our approach is a strategic advantage, reducing the risk of security incidents and enhancing your reputation in the market. With continuous monitoring, we guarantee that your supply chain maintains compliance over time, adapting to evolving regulatory landscapes.


Business Continuity and Resilience
In the intricate realm of supply chain cybersecurity, Wyvern Security's dedication to Business Continuity and Resilience within our C-SCRM strategy is unwavering. We ensure that your operations remain unscathed even in the face of supplier cybersecurity incidents, akin to solving a complex equation for uninterrupted business continuity. This isn't just contingency planning; it's proactive risk mitigation that minimizes financial and reputational risks. We technically prepare your supply chain to deal with disruptions, leveraging redundancy and backup strategies, and our comprehensive planning considers various scenarios, ensuring your operations continue smoothly, no matter the challenges posed by the evolving cybersecurity landscape.
Audit and Compliance Verification
Wyvern Security's commitment to Audit and Compliance Verification within our C-SCRM strategy is unwavering. We ensure the perpetual integrity of your supply chain's robust security fabric through periodic audits that scrutinize supplier cybersecurity practices and contractual compliance. This proactive approach minimizes risks, identifies vulnerabilities promptly, and ensures that your supply chain functions cohesively and securely, much like solving an ongoing mathematical problem. The data-driven insights we provide enable informed decision-making and contribute to the continuous improvement of your cybersecurity practices, fostering a resilient and adaptable security fabric against evolving cyber threats.

Embracing Cybersecurity Supply Chain Risk Management as an ever-evolving process, Wyvern Security champions collaboration, vigilance, and adaptability, aligning your C-SCRM strategy with emerging cyber threats and the dynamic contours of your supply chain. Partner with us for resolute security and unwavering integrity.
